Best Linux distro for privacy and security in 2020
The best Linux distros for privacy and security make it easier to secure your computer against cybersecurity threats, from malware to hacker intrusion attempts.
Best Linux distro for privacy and security
Additionally, privacy and security have become increasing concerns for internet users, not least with increased government monitoring and corporate collection of user data, and a long string of well-publicized hack attacked in which this user data has been stolen and mis-used.
While Windows and macOS computers have some protections in place, and there are additional options such as using a VPN or Tor browser, a number of Linux distros are now available that put privacy and security at their core.
For some of these Linux distros it's a case of building in privacy protection by default using a variety of tools. For others, it's a matter of including security software as standard for those who need to do penetration testing.
Each of these distros has a different focus on privacy and/or security according to user interests and needs. The distros in this guide have all been crafted specifically to equip you with the means to defend your privacy and ensure you stay secure while browsing the internet.
Here therefore we'll list the best Linux distros for privacy and security for you to consider.
- We've also featured the best forensic and pentesting Linux distros.


Linux Administration Bootcamp: Go from Beginner to Advanced, $12.99/£11.99 at Udemy
Learn the ropes of two of the most popular Linux distributions in the world, Red Hat Linux & CentOS, and use the in-demand skills to start a career as a Linux Server Admin or Linux Administrator. The course is presented by Jason Cannon, the author of Linux for beginners, and includes around 500 minutes of in-demand video and four downloadable resources. View Deal

Best privacy and security distros at a glance:
- Want your company or services to be considered for this buyer’s guide? Please email your request to desire.athow@futurenet.com with the URL of the buying guide in the subject line.
- 5 of the most popular Raspberry Pi distros
- Best Linux distros: which one is right for you?
- 10 of the most popular lightweight Linux distros
- These are the best Linux training providers and online courses

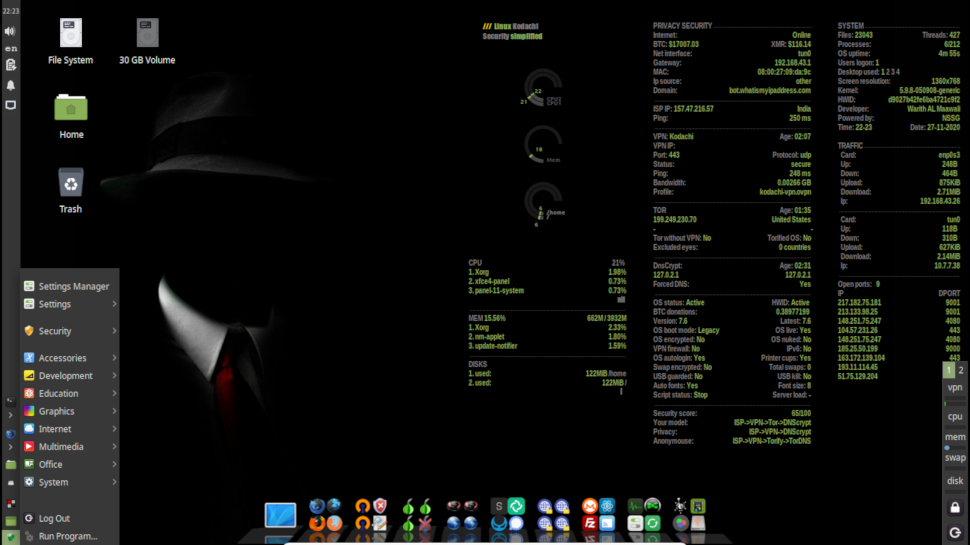
1. Linux Kodachi
Best option for desktop users
Linux Kodachi uses a customized Xfce desktop and aims to give users access to a wide variety of security and privacy tools while still being intuitive. The distro is loaded to the brim with apps that cater to all kinds of users. Kodachi includes all the apps you’ll find on a regular desktop distribution and then some.
To ensure privacy, Kodachi very uniquely routes all your connections to the Internet through a VPN before passing them to the Tor network. Advanced users can also connect via their own VPN.
Kodachi also takes many steps to bolster security. The distro uses AppArmor for application isolation. It also includes an entire suite of privacy-protection tools including VeraCrypt, zuluCrypt, KeePassXC, Metadata Anonymization Toolkit (MAT) for zapping metadata information from files, and more.
The distro also bundles a collection of tools to easily change identifying information such as the Tor exit country. Additionally, the distro encrypts the connection to the DNS resolver and includes well-known cryptographic and privacy tools to encrypt offline files, emails and instant messaging.
The Panic Room entry includes various privacy tools including a tool to wipe RAM, and an option to create a password that when entered will securely erase all contents of your encrypted Kodachi installation.

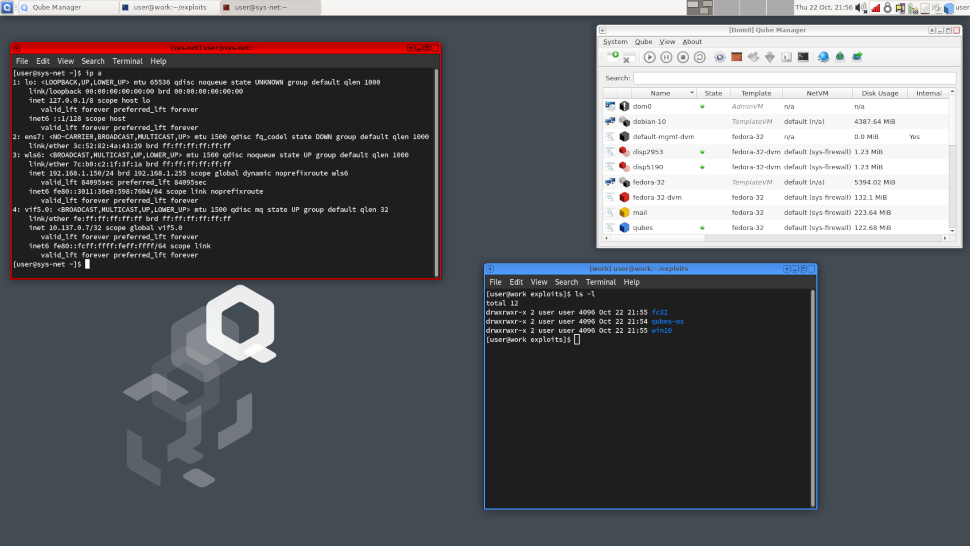
2. Qubes OS
An extremely secure distro, with an innovative user experience
Qubes has established itself as arguably the most popular security-centric distro. It works on the principle of Security by Isolation and makes intelligent use of virtualization to ensure that malicious software doesn’t infect other parts of the installation.
Qubes uniquely isolates several essential elements of the operating system inside different virtual machines, called qubes. An individual instance of an app is restricted within its own qube. Thanks to this arrangement you can run Firefox in one qube to visit untrusted websites and another instance of the browser in a different qube to transact online. A malware ridden website in the untrusted qube will not affect the banking session.
Thanks to its radically different approach, Qubes does have a learning curve. However it isn’t abrupt enough to prevent you from using the distro like a normal Linux installation. Qubes is based on Fedora and uses the Xfce desktop environment. But instead of a list of apps, its application menu lists several qubes such as work, personal, untrusted, each of which rolls the individual apps inside them.

3. Septor
Routes all traffic over Tor
Septor is produced by the Serbian Linux project, which also produces a general purpose Linux distro for Serbian language speakers. Based on Debian’s Testing branch, Septor uses the KDE desktop environment and is one of the newest distros in this guide that’s only had a handful of releases.
To earn its privacy credentials the distro routes all Internet-bound traffic through the Tor anonymous network. Earlier, the distro used a launcher script to fetch the latest Tor release from the Internet, but now bundles it by default.
In addition to the Tor browser, the distro also includes a couple of tools that are designed for use over the Tor network. There’s the anonymous file-sharing program called OnionShare and the Ricochet instant messaging client.
Besides the Tor tools, the distro also has a few other privacy and security enhancing programs such as the Sweeper utility to clear the cache and temporary files, VeraCrypt encryption software and the Metadata Anonymisation Toolkit (MAT).

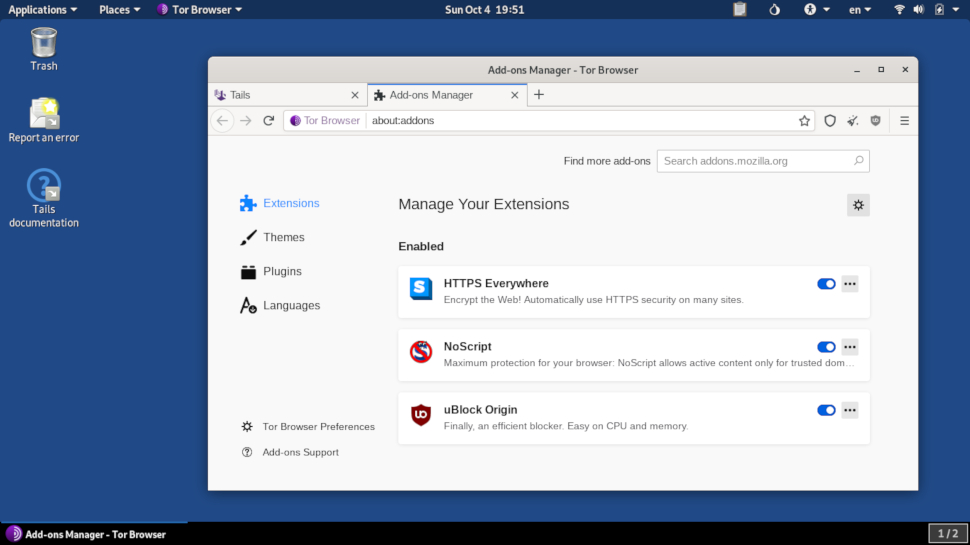
4. Tails
The official distro of the Tor project
Tails (which stands for ‘The Amnesiac Incognito Live System’) is probably the most well-known privacy-focused distro. It can be run from a DVD in Live mode whereby it loads entirely into your system RAM and will leave no trace of its activity. The OS can also be used in ‘persistent’ mode where your settings can be stored on an encrypted USB stick.
All connections are routed through the anonymity network Tor, which conceals your location. The applications in Tails have also been carefully selected to enhance your privacy – for example, there’s the KeePassX password manager and Paperkey, a command line tool used to export OpenPGP secret keys to print on paper. There are also a small number of productivity apps such as Mozilla Thunderbird and the powerful LibreOffice suite.
The distro ships with a number of desktop applications such as LibreOffice, GIMP, Pidgin, Inkscape, Audacity and Thunderbird. You can also utilize the Synaptic Package Manager to flesh out the Gnome-powered distro. Any packages you choose to install aren’t made available at subsequent reboots, unless you configure persistent storage.


5. TENS
Includes a useful tool for encrypting files
Trusted End Node Security (TENS) is designed, developed and distributed by the United States Department of Defense’s Air Force Research Laboratory.
The distro uses the Xfce desktop, which is customized to mimic Windows XP. The layout of the desktop, the placement and naming of the application launcher as well as the window decorations will appear similar to Windows users.
One of the unique aspects of the distro is the Encryption Wizard app. You can drag and drop files inside it and specify a password to lock them. You can also opt to encrypt the files with a certificate file or by generating a secure password to get a stronger passphrase. It uses 128- and 256-bit AES encryption, and supports compression of encrypted archives.
TENS is available in two editions. The Deluxe edition includes the usual desktop productivity apps such as LibreOffice, Totem Movie Player, Evince PDF reader, Firefox, Thunderbird, and more. There’s also a regular release, which includes the encryption app and little else. Unlike the other distros, TENS doesn’t support installation of more software and doesn’t ship with a package manager to flesh out the distro.

6. Whonix
Harness the power of virtual machines to stay safe online
Booting a Live operating system is a nuisance as you have to restart your machine, while installing it to a hard drive means there’s a risk of it being compromised. Whonix offers an elegant compromise by being designed to work as a virtual machine inside the free program Virtualbox.
Whonix is split into two parts. The first ‘Gateway’ routes all connections to the Tor network for the second ‘Workstation’ part. This hugely reduces the chance of DNS leaks which can be used to monitor what websites you visit.
The OS has a number of privacy-conscious features. These include bundled apps such as the Tor Browser and Tox instant messenger.
As it runs in a virtual machine, Whonix is compatible with all operating systems that can run Virtualbox. Virtual machines can only use a portion of your real system's resources, so Whonix will not necessarily perform as fast as an OS that has been installed to a local hard drive.
- Here's our list of the best USB bootable distros
- These are the best Linux repair and rescue distros
- Extend your storage with these best NAS & media server distros
- Experience Arch with these best Arch-based distros
- New to Linux? Here are the best Linux distro for Windows users
- We've featured the best online cybersecurity courses.


No comments